OAuth 2.0 in the Imagicle UCX Suite.
Now that we have a general understanding of what OAuth 2.0 is and what roles are participating, let’s move on to explore the integration within Imagicle services.
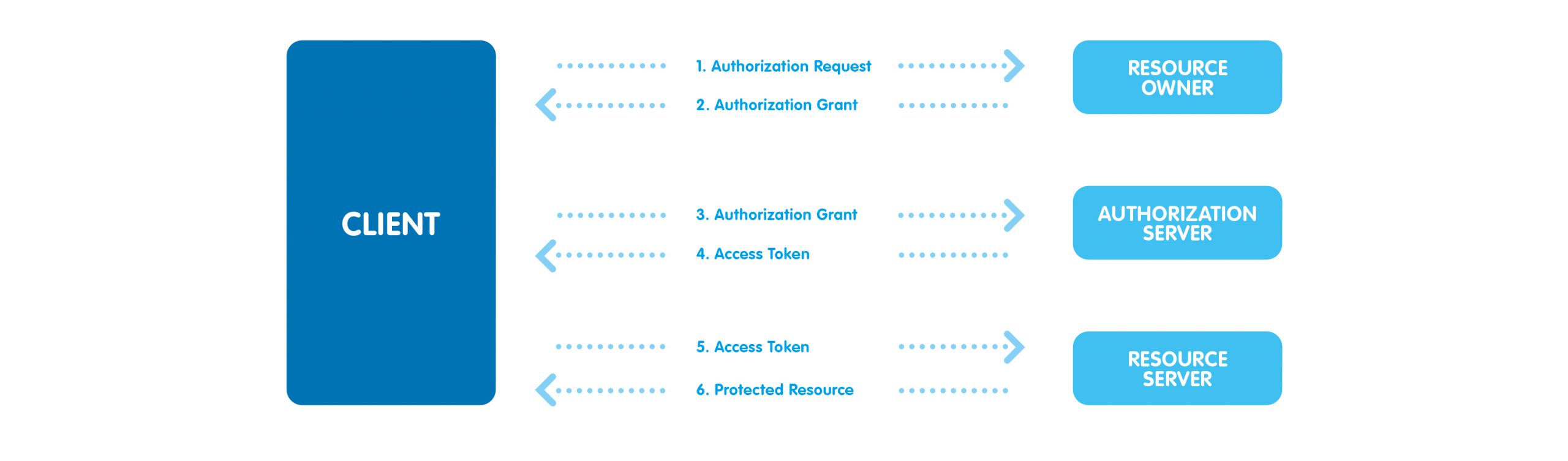
Starting from 2021.Spring.1, we have made integration with Office 365 services more secure with OAuth 2.0. In this particular context, OAuth 2.0 roles are played by:
- Resource Owner: the UCX Suite or Attendant Console user
- Resource/Authorization server: Office 365 services
- Client: Imagicle services, e.g. Digital Fax
Imagicle leverages OAuth 2.0 to connect to Office 365 services. For this reason, if calendar integration or Email To fax were already configured using Office 365 services, upgrading to the latest UCX Suite version this integration will continue to work, guaranteeing greater security and solving the future problem related to the Basic Auth dismission.
Features that currently support it are:
- Digital Fax’s Email to Fax
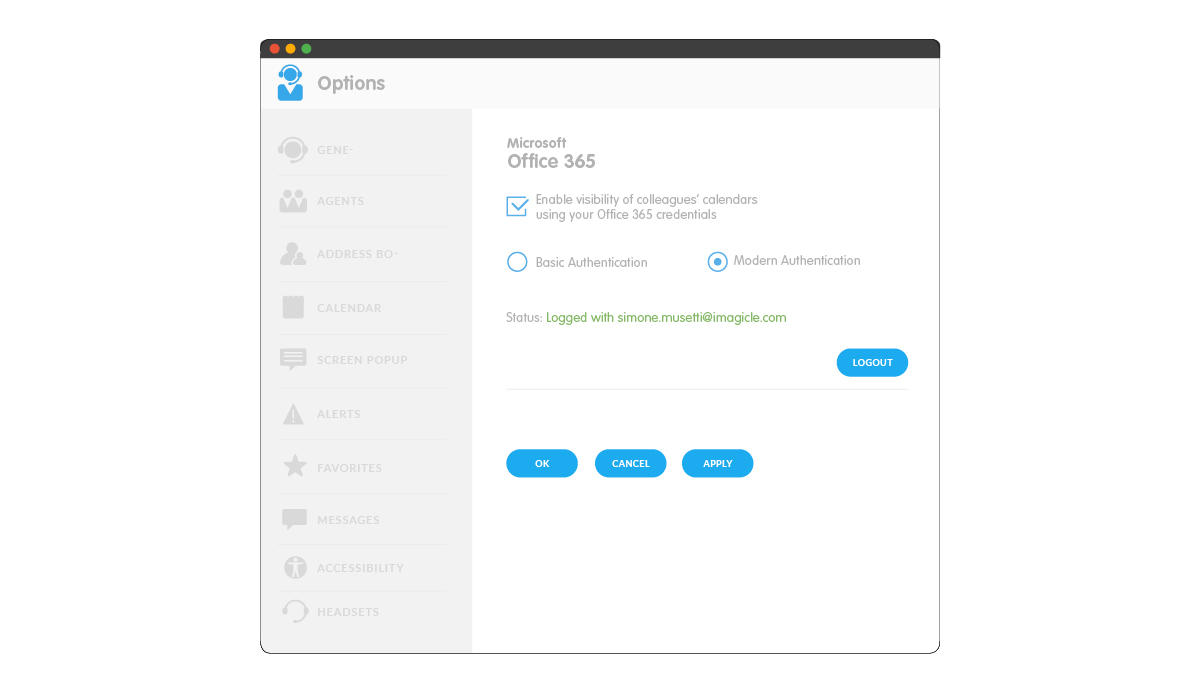
- Calendar integration in Attendant Console
To summarize, when Basic Auth is dismissed from MS you won’t be able to use Email to Fax or the Calendar Integration in our Attendant Console, unless you update your Imagicle UCX Suite to 2021.Spring.1 release.
Let’s look specifically at how individual services leverage this integration.
 Watch
Watch

0 Comments